Blog
Blog Posts
Microsoft issues emergency update for Windows AD Authentication Issues
Microsoft has announced the release of out-of-band updates to address issues with Active Directory authentication issues. These authentication issues occurred as a result of the May 2022 Patch Tuesday updates on domain controllers. Microsoft has worked on issuing an...
QNAP Released Firmware Patches
QNAP, a Taiwan based provider of network-attached storage (NAS) devices announced security updates on Friday that address nine security weaknesses, including a critical issue that could be exploited to take over an affected system. "A vulnerability has been reported...
Hacker Group Targeting Mergers and Acquisitions
An emerging hacker group targeting mergers and acquisitions employees as well as large corporate transactions has appeared in the wild. They appear to have targeted these employees in order to perform email collection activities from victim environments and are...
Russian State-Sponsored Criminal Cyber Threats
Summary The cybersecurity authorities of the US, Australia, Canada, New Zealand and the UK have released a joint Cybersecurity Advisory (CSA). This CSA is to warn organizations about malicious cyber activity originating from Russia as a result of Russia's invasion of...
2021 Top Exploited Vulnerabilities
A joint Cybersecurity Advisory (CSA) released by authorities of the United States, Australia, Canada, New Zealand and the United Kingdom provides details on the top 15 common vulnerabilities and exposures (CVEs). These are vulnerabilities that were routinely exploited...
Ubuntu 22.04 LTS Release – Performance and Security Improvements
Ubuntu 22.04 LTS release (code-named Jammy Jellyfish) has been announced by Canonical Ltd, a UK-based privately held computer software..
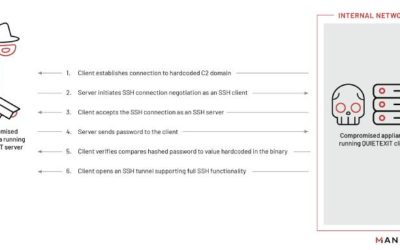
VMware Horizon Actively Exploited Through Log4j2
Iranian Threat Actor "TunnelVision" Actively Exploiting VMware Horizon According to a security adversary from SentinelOne, an Iranian-Aligned threat actor "TunnelVision' is actively exploiting VMware Horizon instances through the use of Log4J2 vulnerabilities....
How To Resolve ‘Sorry but we’re having trouble signing you out’
Are you running into an error such as AADSTS16002 also displayed as 'Sorry but we're having trouble signing you out' ? The fix is easy. You or your users may run into this issue when they try to sign out of Office 365 or its' respective applications such as Azure or...
Wawa Point-of-Sale Malware
A US conenience store, Wawa, said that it discovered malware that skimmed customer’s payment card data at nearly all of its 850 locations.
Johannesburg held for ransom by hacker gang
A hacker group known as the Shadow Kill Hackers is holding Johannesburg, South Africa's largest city, for ransom. They are demanding 4 bitcoins from Johannesburg authorities, or they'll upload stolen city data on the internet. The deadline is October 28, 5 pm, local...
23 Texas Government Agencies Taken Down By Ransomware
Early on August 16, a total of 23 local government organizations in Texas were hit by a coordinated ransomware attack. The type of ransomware has not been revealed, and Texas officials asserted that no state networks were compromised in the attack. State and federal...
Yet Another Exposed Database Found
Researchers said they have found a publicly accessible database containing almost 28 million records—including plain-text passwords, face photos, and personal information—that was used to secure buildings around the world. Researchers from vpnMentor reported on...
Ransomware and malware attacks have more than doubled
Multiple state and local governments have been set back this year onto their heels by ransomware. With attacks like the RobinHood ransomware attack in May that the city is still recoring from, ransomware attacks have been an almost daily part of the news. According to...
48% of Employees Have More Access Than Needed
A new study of over 700 full-time US employees revelead that 48% of employees have access to more company data than they need to perform their jobs. 12% of employees said they have access to all company data. You may have complete trust in your employees but mistakes...
TrickBot Malware Stealing Email Accounts
According to a recent report from Deep Instinct, the Trickbot Malware may have stolen as many as 250 million email accounts including some belonging to governments in the US, UK and Canada. The researchers are calling this new approach TrickBooster, and they say it...
HIPAA Basics For Providers
What's HIPAA? The Health Insurance Portability and Accountability Act (HIPAA) Privacy, Security, and Breach Notification Rules protect the privacy and security of health information. The blog post below will help you understand the HIPAA Basics your business needs to...
What is a vCIO?
IT complexity is a growing challenge for all businesses, regardless of size. The reason is that IT is now integral to virtually every business process. Every company now needs a plan, devised by professionals, for support, security, data protection, business...
4 Things To Know About Securing Your Small Business
Greater Risks for Small Businesses Small businesses often experience a greater risk from hackers, malware and other security threats. We've all seen the headlines, things like 'Data Breach', 'Small vendor a key tool used in a bigger attack' and others. Small...
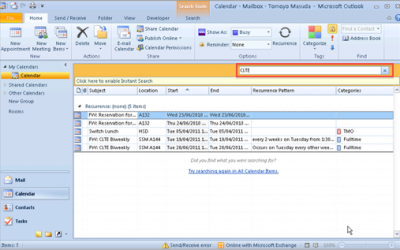
Automatic Printing of Attachments in Outlook
Outlook can be configured to automatically print attachments from incoming emails. To do that you need to add a script in Outlook by following the instructions below. Once you've performed all of these steps, Outlook will automatically print attachments from incoming...
Hundreds of US schools still vulnerable to WannaCry
Wondering why ransomware continues to be such a problem for state and local governments and other public institutions? Publicly accessible security-scan data shows that many public organizations have failed to do more than put a bandage over long-standing system...
Value of IT Security in Business
The Problem Business leaders do not always see the value when it comes to IT Security. They often do not see it as a competitive advantage either. Even though high-profile cases (hacks, ransomware attacks etc.) help, the vast majority continue to operate under the "it...
Protecting your business email account explained
Background Over the last year, cyber criminals have continued to increase their use of social engineering rather than automated exploits, scaling up people-centered threats and attacks that rely on human interaction. They have found new ways to exploit “the human...
Best Practices for Dealing With Phishing and Ransomware
Phishing and ransomware are serious problems that can steal and disable access to corporate finances, sensitive employee data, patient data, intellectual property, employee files and other valuable content. Both ransomware and phishing attacks and their variants are...
Business Password Security Checklist
Business Password Security Explained Protecting your business from data theft and malicious attacks doesn't have to be hard. Simply following the password security checklist (further down in this post) can greatly improve the security of your business at no cost to...
We're Here To Help!
Office
Bensenville, IL 60106
Hours
S-S: Closed