Blog
Blog Posts
Developing an IT Strategy for Your Business
In this comprehensive blog article, we will explore the key components involved in developing an IT strategy for your business, outlining a step-by-step guide to navigate the complexities of aligning IT initiatives with overarching business goals.
Cyber Security Training Benefits
In this extensive blog article, we will explore what cyber security training for employees entails, delve into the multifaceted benefits of such training, analyze the return on investment (ROI) for organizations, underscore the importance of running regular mock phishing campaigns, and emphasize the critical role of choosing an IT provider that can assist in training employees to fortify the organization’s cyber defenses.
DFARS Compliance : A Guide
In this comprehensive blog article, we will explore what DFARS compliance entails, delve into the benefits of achieving DFARS compliance, examine the protective measures it offers, and underscore the crucial importance of choosing an IT provider such as ATYXIT that can assist organizations in their journey toward DFARS compliance.
Benefits of a Managed SOC
In this extensive blog article, we will explore what a managed SOC is, delve into its key features, examine the protection it provides against cyber attacks, discuss the reasons businesses should outsource their IT security, analyze the cost savings derived from outsourcing, and underscore the critical importance of choosing an IT provider with a proven track record in managing the cybersecurity of businesses.
The Power of Private Cloud Services
In the dynamic landscape of business technology, private cloud services have emerged as a game-changer, providing organizations with a secure, flexible, and cost-effective solution for their computing needs.
A Comprehensive Guide to Smokeball Practice Management Software
Smokeball, a leading legal practice management software, stands at the forefront of innovation, offering a comprehensive suite of features tailored to meet the unique needs of legal professionals.
Importance of a Business Phone Audit
In this article, we will explore four compelling reasons why small businesses should conduct a regular business phone audit. The focus will be on reviewing billing issues, identifying problem callers, reducing monthly costs, and contemplating the possibility of transitioning to hosted VoIP.
Elevating Small Businesses: Eight Reasons to Move to the Cloud
This article explores the compelling reasons behind the decision to move to the cloud, shedding light on key advantages such as ease of usage and scalability, reduced cost of ownership, streamlined maintenance, staying online with redundant internet providers, enhanced data security, and the built-in disaster recovery capabilities.
Why and How: Testing Data Backups
Data is the lifeblood of small businesses, making the integrity and availability of that data paramount. A crucial aspect of maintaining a robust data management strategy is regularly testing data backups. In this comprehensive article, we will delve into the significance of testing data backups for small businesses
Why Switch To VoIP?
This article delves into three compelling reasons why small businesses should make the switch to VoIP, exploring the technology’s fundamental aspects, increased productivity through advanced functionalities and unified communications, mobility and scalability, lower cost of ownership, backup internet options, and why VoIP is poised to be the future of business telephony.
Hosted VoIP Benefits Explained
Hosted VoIP (Voice over Internet Protocol) emerges as a game-changer, offering a myriad of benefits that can significantly elevate communication efficiency. In this article, we’ll explore hosted VoIP benefits and ultimately showcase why hosted VoIP is the superior choice for SMBs, touching on essential features such as cost savings, flexibility, ease of management, device compatibility, advanced functionalities, and the luxury of an interactive virtual receptionist.
Installing Let’s Encrypt on cPanel
Easy to follow how-to information on installing Let’s Encrypt on cPanel. Secure all of your company websites today by following this simple guide.
How to Use Yammer Groups in Office 365
Yammer Groups in Office 365 offer a streamlined and effective way to enhance communication and collaboration within organizations. By leveraging the power of Yammer, teams can work together seamlessly, regardless of their location or time zone.
Boosting Your Chicago Business with an Effective Call Center Solution
One effective tool that can help them achieve this is a well-planned call center solution. Call centers have become increasingly important for Chicago businesses, offering them a wide range of benefits and advantages.
Unveiling the Reality of Software Renewals
Software renewals are an integral part of managing and maintaining a company’s digital infrastructure. However, there is often more to software renewals than meets the eye. In this article, we will delve into the intricacies of such renewals and uncover the underlying reality behind them.
A Step-by-Step Guide to Create QR Codes for Your Business
In this article, we will take a closer look at the basics of QR codes, how to create QR codes for your business, and the latest advancements in QR code technology. We will also discuss the importance of choosing the right IT partner for your business to navigate through the intricacies of QR code implementation successfully.
Automate Outlook Email Attachment Printing
However, there is a way to streamline this process and make it more efficient – by automating Outlook email attachment printing. With this innovative solution, you can save time and ensure that your workflow remains uninterrupted.
Ultimate Guide to Business Computer Help
In this ultimate guide, we will explore the key components of business computer systems, the importance of regular system updates, choosing the right business computer help, implementing effective computer maintenance practices, enhancing business operations with computer software, and securing your business computers against cyber threats.
Small Business IT Services Guide
Looking to streamline your small business IT services? Discover expert tips, best practices, and cost-effective solutions to optimize your technology infrastructure and boost productivity in this comprehensive article..
The Ultimate Guide to Small Business IT Services
Small business IT services come in various forms, each tailored to address specific technology aspects and business requirements. Understanding these different types will help you identify which ones align with your needs and contribute to your business success.
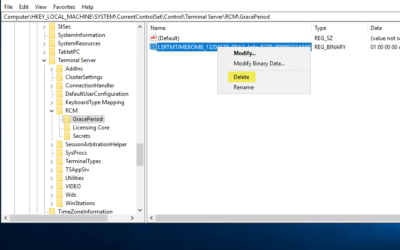
Windows Server: Reset RDS Grace Period
Thankfully, there’s a “hack” that allows you to reset the expiration of Remote Desktop Services (RDS) grace period on Microsoft Windows Server, effectively rewinding the clock on your RDS licensing. This should only really be used if you’re using RDS in a lab environment. Completing the steps you see below guarantees that you reset RDS grace period without having to reinstall or re-creating any virtual machines.
New SEC requirements for cyberattack disclosures
SEC Requirements for Cyberattack Disclosures by Publicly Traded Companies U.S. Securities and Exchange Commission The U.S. Securities and Exchange Commission (SEC) has implemented new regulations mandating prompt disclosures of cyberattacks for publicly traded...
Rise in USB drive malware attacks
In the first half of 2023, there has been a notable resurgence of USB drive malware distribution, demonstrating that what’s old is new again. Researchers have witnessed a threefold increase in this method, revealing the persistence and detection evasion techniques employed by cybercriminals.
Role of a vCIO in Managed IT Services
The Role of a vCIO in Managed IT Services: Unlocking Strategic Technology Leadership for Businesses. A vCIO, or virtual Chief Information Officer, is a senior-level technology executive who collaborates with businesses as an outsourced IT consultant,
We're Here To Help!
Office
Bensenville, IL 60106
Hours
S-S: Closed