In the first half of 2023, there has been a notable resurgence of USB drive malware distribution, demonstrating that what’s old is new again. Researchers have witnessed a threefold increase in this method, revealing the persistence and detection evasion techniques employed by cybercriminals.
Security Reports
Mandiant, a leading cybersecurity company, has released a report outlining two prominent USB drive malware campaigns observed this year. The first campaign, named ‘Sogu,’ has been attributed to a Chinese espionage threat group called ‘TEMP.HEX.’ Sogu is currently the most aggressive USB-assisted cyber-espionage campaign, targeting industries worldwide with the primary objective of stealing valuable data. The victims of Sogu malware are located in a wide range of countries, including the United States, France, the UK, Italy, Poland, Austria, Australia, Switzerland, China, Japan, Ukraine, Singapore, Indonesia, and the Philippines. The sectors affected vary from pharmaceuticals and IT to energy, communications, health, and logistics.
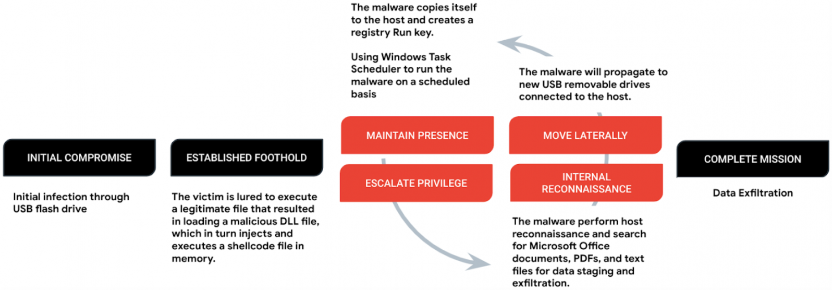
Sogu malware achieves persistence through various means, including the creation of a registry Run key and the utilization of Windows Task Scheduler to ensure regular execution. It employs a payload called ‘Korplug,’ which loads C shellcode into memory via DLL order hijacking, necessitating the victim’s execution of a legitimate file. Once established, Sogu conducts system reconnaissance by dropping a batch file onto ‘RECYCLE.BIN,’ scanning for valuable data contained in MS Office documents, PDFs, and other text files. The discovered files are encrypted using base64 and copied to both the host’s C:\ drive and the working directory on the flash drive. The exfiltration of these document files to the command-and-control (C2) server occurs over TCP or UDP using HTTP or HTTPS requests.
Sogu’s capabilities extend beyond data theft, with support for command execution, file execution, remote desktop access, screenshot capturing, establishing reverse shells, and keylogging. Notably, any connected drives automatically receive a copy of Sogu’s initial compromise file to facilitate lateral movement within the network through USB drive malware.
Snowydrive
Another campaign highlighted by Mandiant is ‘Snowydrive,’ attributed to UNC4698, which specifically targets oil and gas firms in Asia. Snowydrive infects computers through a backdoor mechanism that enables attackers to execute arbitrary payloads, modify the registry, and perform file and directory actions. Similar to Sogu, Snowydrive relies on deceiving victims into launching what appears to be a legitimate executable on a USB drive. This action triggers the extraction and execution of the malware components stored within a folder named ‘Kaspersky.’ The backdoor, which is based on shellcode, loads into the process of a legitimate archive unzip software called ‘CUZ.exe.’
Snowydrive’s backdoor offers various commands for file operations, data exfiltration, reverse shell setup, command execution, and reconnaissance. To evade detection, the malware utilizes a malicious DLL side-loaded by a legitimate Notepad++ updater named ‘GUP.exe.’ This technique allows Snowydrive to conceal file extensions and protect specific files labeled as “system” or “hidden.”
USB Drive Malware Traction
These USB-based attacks continue to gain traction in 2023 due to their ability to bypass security mechanisms, remain stealthy, gain initial access to corporate networks, and even infect air-gapped systems that are isolated from unsecured networks for enhanced security. Mandiant’s investigation reveals that print shops and hotels often serve as infection hotspots for USB malware. It is essential to recognize that given the random and opportunistic nature of these backdoors, any system equipped with a USB port becomes a potential target.
Moreover, it is worth noting that in November 2022, Mandiant had already highlighted a USB-based campaign originating from China, which utilized USB devices to infect entities in the Philippines with four distinct malware families. Additionally, in January 2023, the Unit 42 team from Palo Alto Networks uncovered a variant of PlugX malware capable of hiding within USB drives and infecting connected Windows hosts. These reports further emphasize the growing threat posed by USB-delivered malware and the need for robust cybersecurity measures to mitigate these risks.
ATYXIT provides every one of our partners with a Cyber Security stack that outperforms all these viruses and malicious attacks functions and helps ensure the technology in your business continues to function, just like your business.
Contact us to improve the way your business does technology.
We Make IT Easy. See the areas we service.

