Blog
Blog Posts
The Dangers of Using Password Managers
In an age where nearly every website requires a login, password managers have become a go-to solution for simplifying online security. They promise to create, store, and manage your passwords safely, but not all promises hold up under scrutiny. As convenient as these tools are, understanding the dangers of using password managers is essential before you entrust them with your digital life.
Business Technology in 2026
In 2026, small and mid-sized businesses are under pressure to modernize around AI, cloud, and cybersecurity while keeping costs and risk under control. A provider like ATYXIT can act as a strategic IT partner to plan, implement, and support these changes without...
Business Cloud Backup Guide
Looking for an easy business cloud backup guide? Cloud backups have become one of the most important layers of protection for modern businesses. Instead of relying on a single server, office PC, or external hard drive, cloud backups quietly and consistently copy your critical data to secure, off‑site locations where it can be restored quickly if something goes wrong.
How often should a business replace computers and servers?
Are you wondering how often a business should replace computers and servers? A structured replacement cycle turns IT from a constant headache into a predictable investment that supports growth in your business.
Signs it’s time to change IT providers.
This post walks through clear red flags that your current IT support is letting you down and the signs showing it may be time to change IT providers.
IT Consulting for Startups : Guide
Every decision can be a make-or-break moment, especially when it comes to technology. For fledgling companies launching innovative ideas, navigating the complex landscape of IT infrastructure, cybersecurity, and cost management can feel like solving a Rubik’s Cube blindfolded. That’s where IT consulting for startups from experts like ATYXIT steps in—not just as a lifesaver but as a strategic partner empowering startups to conquer technological hurdles efficiently and affordably.
Attorney IT Services Explained
Attorney IT services encompass management of the entire technological infrastructure used by law firms, including networking, servers, cloud storage, and security. For law firms, this means their IT infrastructure is continuously monitored, maintained, and optimized to ensure minimal downtime and maximal data protection.
IT Infrastructure Management : Backbone of Business Efficiency
At the heart of managing these complex systems lies IT infrastructure management, a discipline focused on maintaining, optimizing, and scaling an organization’s technological backbone. For firms like ATYXIT, this service ensures businesses remain agile, secure, and cost-efficient while staying focused on their core objectives.
Volume of Ransomware Attacks in 2025
The volume of ransomware attacks in 2025 was up by 179% compared to the same period in 2024, according to statistics published by threat intelligence platform provider Flashpoint.
The past year has seen significant changes among cyber criminal threat actors with previously feared groups such as LockBit – taken down by law enforcement and others no longer the forces they once were.
PowerSchool Data Breach Explained
The recent PowerSchool data breach has sent shockwaves through the education sector, exposing sensitive information of millions of students and teachers across North America. This massive cyberattack, discovered in late December 2024, has affected thousands of school districts and highlighted the urgent need for improved cybersecurity measures in educational institutions.
Quarterly Backup Testing – Why and How?
This is where the importance of regular backup testing comes into play, and specifically, why quarterly backup testing should be a non-negotiable part of your IT strategy even if you utilize a Managed IT Provider.
24/7 IT Support Benefits
As technology continues to be the backbone of modern enterprises, 24/7 IT support offers a multitude of benefits that can significantly impact a company’s success and longevity.
Chicago Outsourced IT
A Chicago outsourced IT provider in should offer a comprehensive suite of services to ensure businesses stay on top of their technology needs while implementing and maintaining robust security.
Best Business Firewall Comparison
Based on extensive research among network engineers and IT administrators, ATYXIT has come up with a list of firewalls in order to determine the best business firewall. Here are the most commonly used firewalls in businesses in 2024, along with their pros and cons: 1....
Cybersecurity Audit: Business Guide
A Comprehensive Guide to Performing a Cybersecurity Audit for Businesses In today's digital landscape, cybersecurity audits have become essential for businesses that want to protect their assets, data, and reputation. This guide will walk you through the process of...
Implementing Business 2FA
Implementing business 2FA (two-factor authentication) is a crucial step in enhancing cybersecurity at your organization. Here’s a comprehensive guide with some tips on rolling out 2FA effectively across all your employees:
Useful PowerShell Commands
PowerShell has become an essential tool for Windows Server and Active Directory management. Here’s a guide to some of the most useful PowerShell commands for these types of environments that are guaranteed to make both your life and management easier.
The Role of Employee Cybersecurity Training
In today’s digital landscape, where cyber threats are becoming increasingly sophisticated and prevalent, employee cybersecurity training alongside immutable backups has emerged as a critical component of a robust defense strategy for businesses.
Ransomware Recovery Guide
This article explores the role of data backups, particularly immutable backups, in protecting businesses from ransomware attacks and provides a ransomware recovery guide that covers the the recovery process for companies with and without proper backup strategies.
Business Technology in 2025
The business technology in 2025 is poised for significant transformation. From artificial intelligence to sustainability initiatives, companies are gearing up for a future that promises both exciting opportunities and complex challenges.
Understanding the Fortigate Vulnerability
In today's digital landscape, cybersecurity threats are evolving at an unprecedented pace, posing significant risks to businesses of all sizes. Recently, a critical vulnerability in Fortinet's FortiManager, identified as CVE-2024-47575, has highlighted the urgent need...
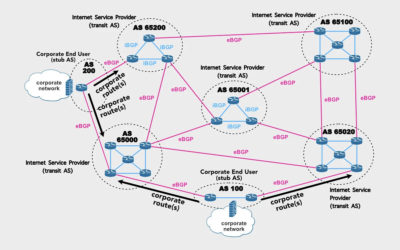
The White House on BGP Security
Recognizing the urgent need to address these vulnerabilities, the Biden administration has unveiled a comprehensive strategy to enhance BGP security.
YubiKey Vulnerability Discovered
A YubiKey vulnerability discovered! YubiKeys, popular security devices used for two-factor authentication, have been found to be vulnerable to cloning attacks. This discovery was made by researchers from the NinjaLab in France.
CrowdStrike Response to Outage
CrowdStrike, a prominent cybersecurity firm, recently faced criticism from its competitors following a major software update failure that led to a global IT outage. Michael Sentonas, CrowdStrike’s president, expressed his discontent with what he described as “shady” tactics employed by rival companies attempting to capitalize on the situation by instilling fear among CrowdStrike’s customers and capturing market share.
We're Here To Help!
Office
Bensenville, IL 60106
Hours
S-S: Closed