
Jan 20, 2024 | Business IT Tips
Running a successful business today often relies heavily on the effective use of computer systems. From managing operations to storing critical data, business computers play a crucial role in ensuring smooth day-to-day operations. However, attempting to find the right...

Jan 20, 2024 | Business IT Tips
In today’s digital age, small businesses are increasingly reliant on technology to streamline their operations, improve productivity, and stay competitive in the market. However, managing and maintaining an efficient IT infrastructure can be a daunting task for...
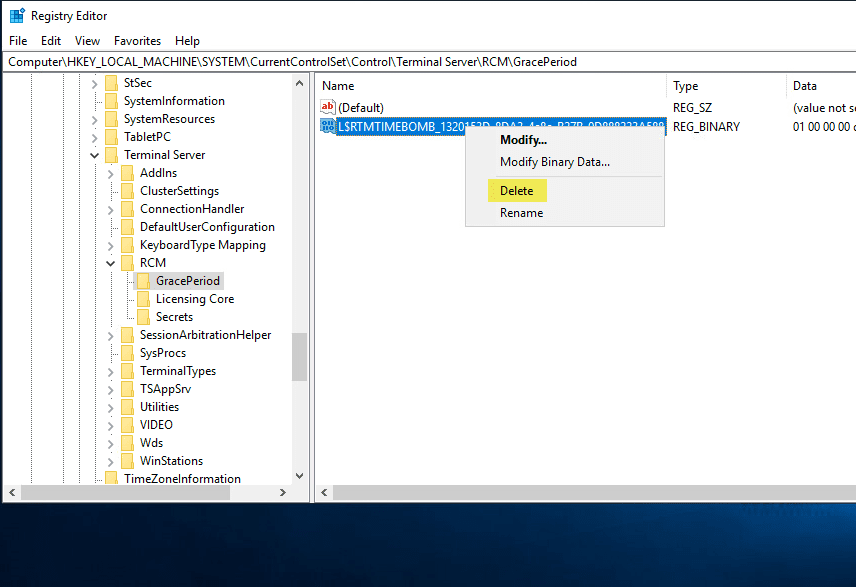
Jul 30, 2023 | Business IT Tips
How to Reset RDS Grace Period on Windows Server 2016 and 2019 If you’re running a home lab or any testing environment, you might encounter challenges with licensing and trial expiration. Thankfully, there’s a “hack” that allows you to reset the...

Apr 13, 2023 | Business IT Tips
The Role of a vCIO in Managed IT Services: Unlocking Strategic Technology Leadership for Businesses Nowadays, businesses of all sizes and industries rely heavily on technology to operate efficiently and stay competitive in the market. However, managing IT...

Mar 5, 2023 | Business IT Tips
As businesses become increasingly reliant on technology, the importance of cyber security is increasing as well. Cyber security has become an essential part of any successful business. Cyber-attacks are constantly evolving, and businesses must stay ahead of the curve...






