
Oct 20, 2025 | Business IT Tips
IT Infrastructure Management: The Backbone of Modern Business Efficiency In today’s digitally driven economy, the strength and reliability of a company’s IT infrastructure define its ability to compete. Networks, servers, storage, and cloud environments all work...

Aug 26, 2025 | Business IT News
The volume of ransomware attacks in 2025 was up by 179% compared to the same period in 2024, according to statistics published by threat intelligence platform provider Flashpoint. The past year has seen significant changes among cyber criminal threat actors with...
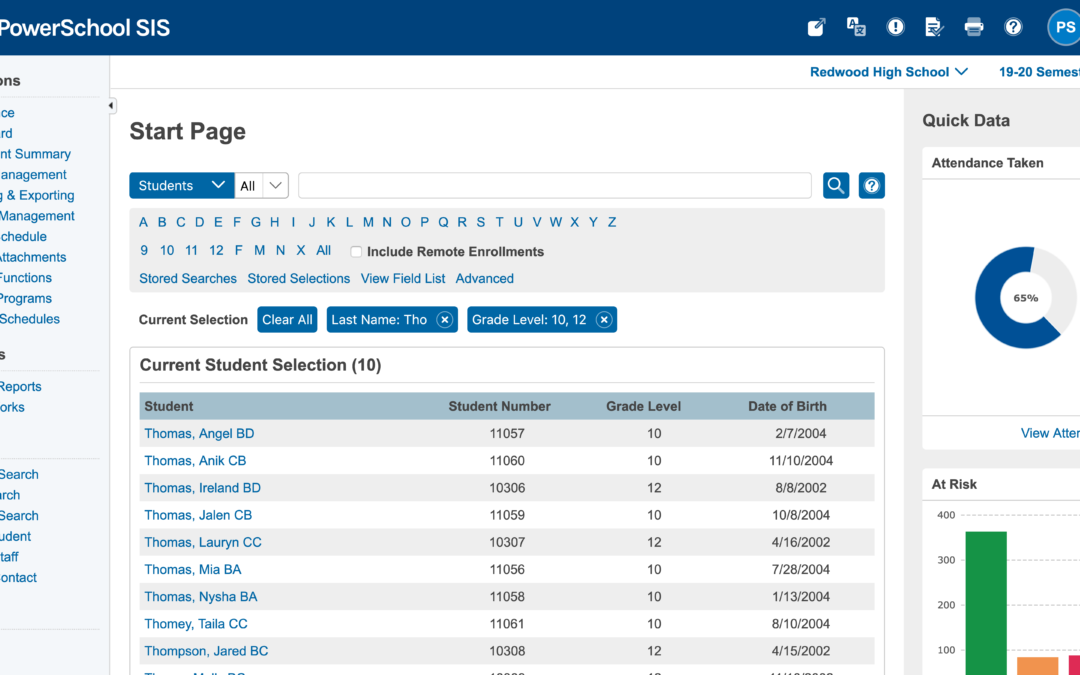
Feb 6, 2025 | Business IT News
The recent PowerSchool data breach has sent shockwaves through the education sector, exposing sensitive information of millions of students and teachers across North America. This massive cyberattack, discovered in late December 2024, has affected thousands of school...

Jan 30, 2025 | Business IT Tips
The Power of 24/7 IT Support: Fueling Chicago’s Business Success In the bustling metropolis of Chicago, where business never sleeps, the need for round-the-clock IT support has become increasingly crucial. As technology continues to be the backbone of modern...

Jan 26, 2025 | Business IT Tips
Based on extensive research among network engineers and IT administrators, ATYXIT has come up with a list of firewalls in order to determine the best business firewall. Here are the most commonly used firewalls in businesses in 2024, along with their pros and cons: 1....






