An emerging hacker group targeting mergers and acquisitions employees as well as large corporate transactions has appeared in the wild. They appear to have targeted these employees in order to perform email collection activities from victim environments and are suspected of engaging in espionage.
Mandiant, a publicly traded American cybersecurity firm, is tracking this activity under the uncategorized moniker UNC3524, citing a lack of evidence linking it to an existing group. Some of the intrusions, however, are said to mirror techniques used by different Russian-based hacking crews like APT28 and APT29.
Mandiant announced on March 8th of 2022 that it was being acquired by Google LLC in an all-cash transaction valued at approximately $5.4 billion. The offer represented a 57% premium to the share price at the time of the agreement.
“The high level of operational security, low malware footprint, adept evasive skills, and a large Internet of Things (IoT) device botnet set this group apart and emphasize the ‘advanced’ in Advanced Persistent Threat,” the threat intelligence firm announced in a Monday report.
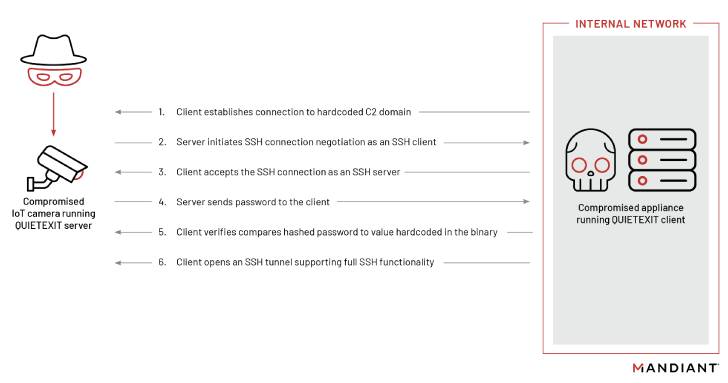
The process behing the initial malicious entry is unknown but upon establishing a foothold, attack chains involving UNC3524 result in the deployment of a novel backdoor called QUIETEXIT for persistent remote access. Some of these occurrences have lasted for as long as 18 months without the UNC3524 group being detected. The longer an attacker has access to your system, the higher the chance they will continue to traverse further down your network and compromise more systems. This is the primary reason you should be partnering with a trusted IT Partner that leverages state of the art Cybersecurity solutions.
It’s also important to remember that no amount of cybersecurity can replace a working data backup & disaster recovery solution with off-site redundancy.
The hacker group targeting mergers and acquisitions companies utilizes a botnet of internet-exposed IP camera devices in order to blend in with legitimate traffic. The threat actor also installs a web shell as an alternative means of access should the primary backdoor be detected and removed.