
Jan 18, 2025 | Business IT Tips
The Crucial Role of Employee Cybersecurity Training in Protecting Businesses In today’s digital landscape, where cyber threats are becoming increasingly sophisticated and prevalent, employee cybersecurity training alongside immutable backups has emerged as a...

Jan 3, 2025 | Business IT News
The business technology in 2025 is poised for significant transformation. From artificial intelligence to sustainability initiatives, companies are gearing up for a future that promises both exciting opportunities and complex challenges. Let’s explore the key...
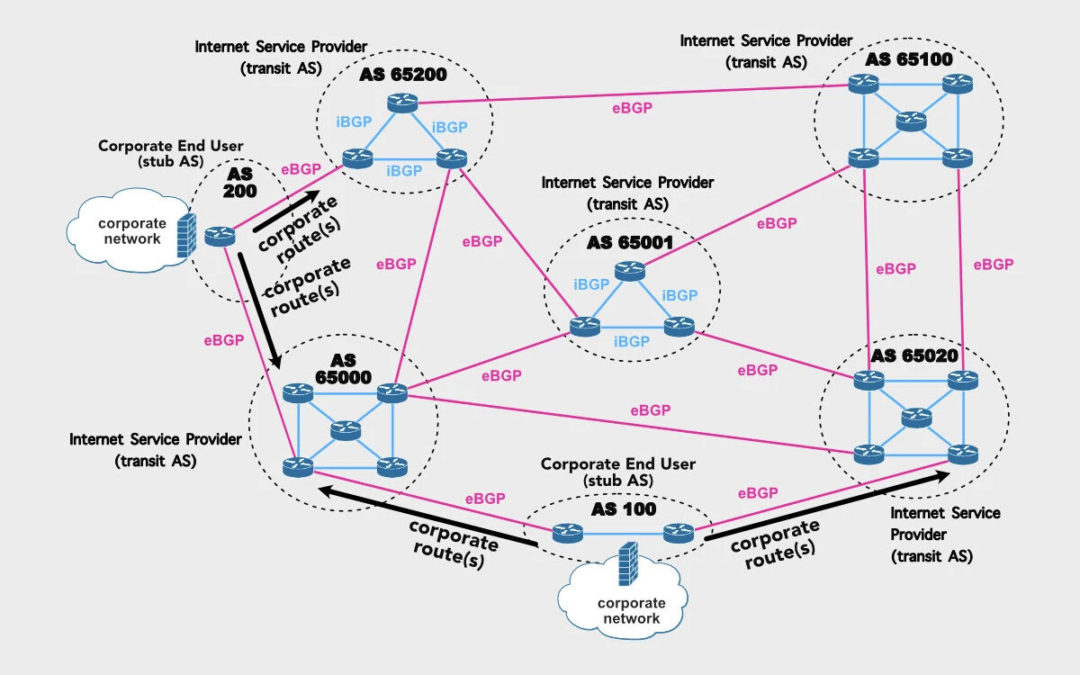
Sep 6, 2024 | Business IT News, Security Advisories
In an era where cybersecurity threats loom larger than ever, The White House has taken a significant leap forward in addressing one of the Internet’s most critical vulnerabilities. The Border Gateway Protocol (BGP), the backbone of internet routing, has long...

Sep 4, 2024 | Business IT News, Security Advisories
A YubiKey vulnerability discovered! YubiKeys, popular security devices used for two-factor authentication, have been found to be vulnerable to cloning attacks. This discovery was made by researchers from the NinjaLab in France. What are YubiKeys? YubiKeys are small...

Sep 2, 2024 | Business IT News
CrowdStrike, a prominent cybersecurity firm, recently faced criticism from its competitors following a major software update failure that led to a global IT outage. Michael Sentonas, CrowdStrike’s president, expressed his discontent with what he described as...






