
Jan 13, 2026 | Business IT News, Business IT Tips
In 2026, small and mid-sized businesses are under pressure to modernize around AI, cloud, and cybersecurity while keeping costs and risk under control. A provider like ATYXIT can act as a strategic IT partner to plan, implement, and support these changes without...

Aug 26, 2025 | Business IT News
The volume of ransomware attacks in 2025 was up by 179% compared to the same period in 2024, according to statistics published by threat intelligence platform provider Flashpoint. The past year has seen significant changes among cyber criminal threat actors with...
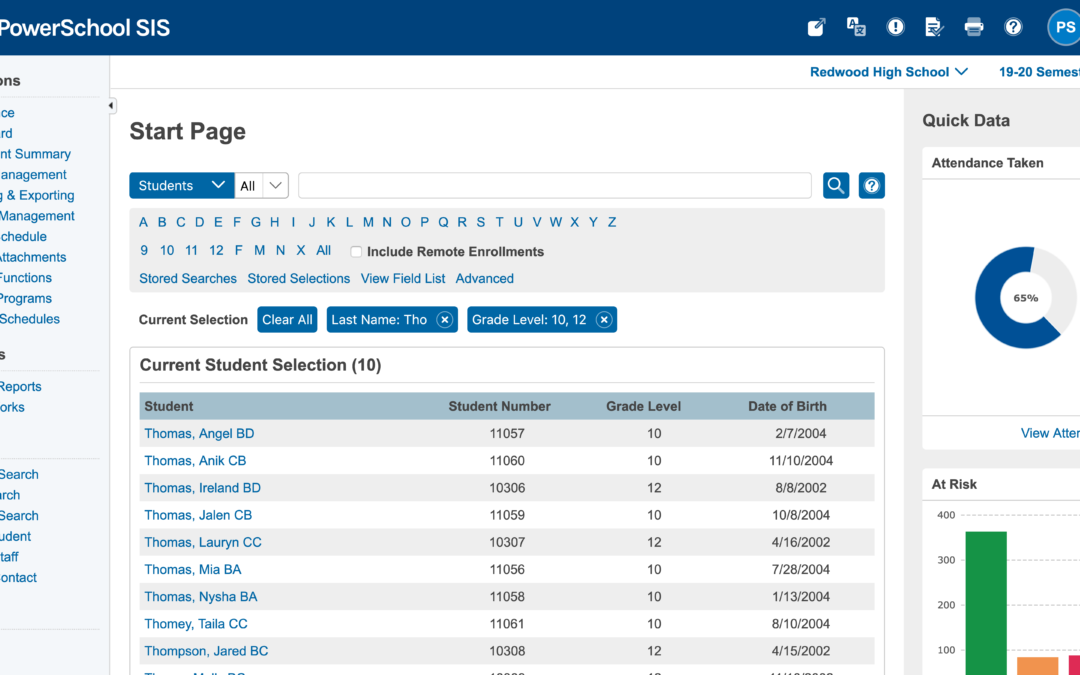
Feb 6, 2025 | Business IT News
The recent PowerSchool data breach has sent shockwaves through the education sector, exposing sensitive information of millions of students and teachers across North America. This massive cyberattack, discovered in late December 2024, has affected thousands of school...

Jan 3, 2025 | Business IT News
The business technology in 2025 is poised for significant transformation. From artificial intelligence to sustainability initiatives, companies are gearing up for a future that promises both exciting opportunities and complex challenges. Let’s explore the key...
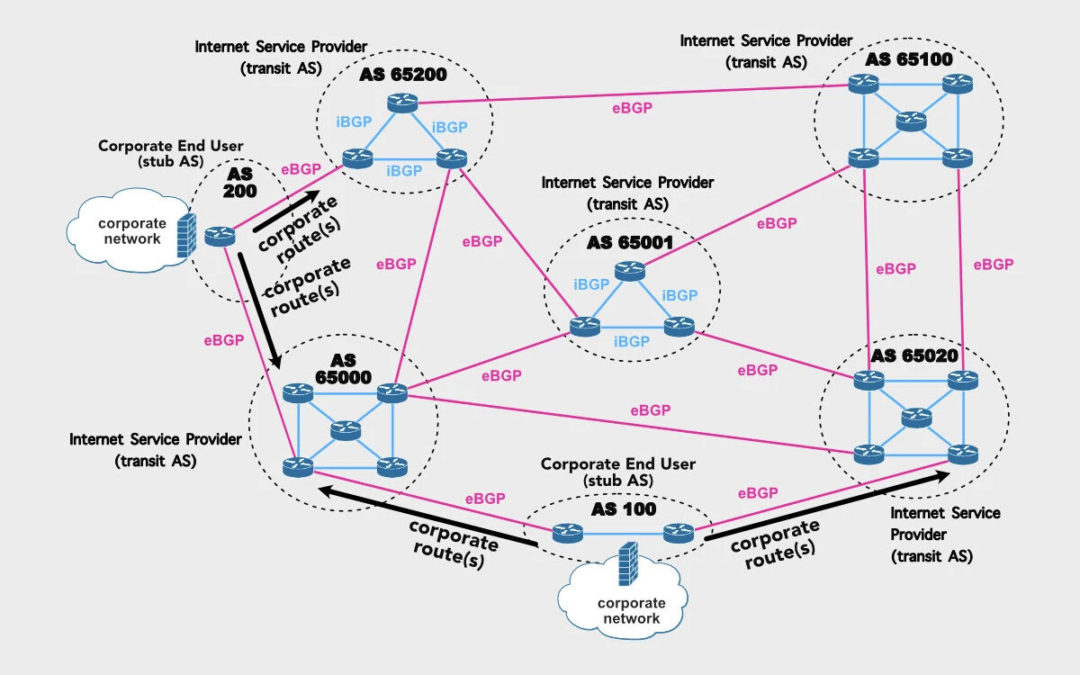
Sep 6, 2024 | Business IT News, Security Advisories
In an era where cybersecurity threats loom larger than ever, The White House has taken a significant leap forward in addressing one of the Internet’s most critical vulnerabilities. The Border Gateway Protocol (BGP), the backbone of internet routing, has long...

Sep 4, 2024 | Business IT News, Security Advisories
A YubiKey vulnerability discovered! YubiKeys, popular security devices used for two-factor authentication, have been found to be vulnerable to cloning attacks. This discovery was made by researchers from the NinjaLab in France. What are YubiKeys? YubiKeys are small...







